Manufacturing Tops Industrial Ransomware Hit List in 2021
Manufacturers are increasingly targeted for attack as cyber criminals refine their ransomware and adopt new business models to fund their operations.

Last year ransomware gangs turned up the heat against all industrial sectors, but manufacturers have the most to worry about amid this distressing rash of cyber extortion. The statistics show that in 2021 adversaries targeted manufacturing with industrial ransomware nearly twice as often as all the other industrial sectors combined.
It’s a trend that shows no sign of slowing down as adversaries increasingly recognize manufacturers as extremely profitable targets for ransomware schemes that encrypt and disable operational technology (OT) systems on the factory floor and beyond, requiring victims to pay for the keys to decrypt their files and restore functionality to their systems. Savvy ransomware groups recognize the value of uptime in the manufacturing industry and they’re ruthlessly profiting on the fact that manufacturers are often the least mature in their OT defenses compared to other industrial verticals.
Manufacturing Ransomware Statistics
Dragos identified the intensification of manufacturing ransomware through data compiled for its 2021 ICS/OT Cybersecurity Year in Review (YiR) report, an annual compendium of OT security statistics and observations.
YiR findings showed 2021 as a pivotal year for ransomware groups targeting OT systems, with ransomware becoming the number one driver for compromises in industrial environments. Weak boundaries and poorly understood interactions between OT and IT systems, coupled with the rise in remote access—especially as more organizations rely on their work-from-home staff—contributed to industrial ransomware’s rising trend lines.
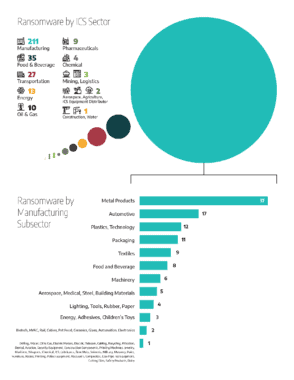
Broken down by industrial sector, manufacturing accounted for 65% of all the industrial ransomware incidents last year. Manufacturers suffered six times as many industrial ransomware incidents as the second leading sector, food and beverage, which suffered about 11% of last year’s attacks. Transportation came in third, accounting for about 8% of industrial ransomware attacks in 2021.
Digging deeper into the category of manufacturing ransomware incidents, the top three most common subsectors impacted by these attacks were Metal Components (17%), Automotive (8%), and Plastics/Technology (6%).
Rise in Ransomware Attacks
While ransomware still mainly targets enterprise IT systems, Dragos intelligence shows there are growing instances of these attacks that impact OT directly and in integrated IT and OT environments. Often ransomware adversaries indirectly attack OT systems as targets of opportunity after gaining initial access in adjacent and integrated IT systems. They use the compromise of critical enterprise IT systems to move laterally into OT. Some ransomware groups specifically target OT systems.
For example, EKANS is a specific ICS targeted ransomware that has gone after companies across electric, oil and gas, medical and pharmaceutical manufacturing, and automotive sectors. Dragos analyzed multiple variants of EKANS malware and discovered that the EKANS variant has the ability to stop ICS-related Windows processes before initiating encryption.
In 2021 the most prolific ransomware groups to attack OT systems were Conti and Lockbit 2.0, which caused 51 percent of total ransomware attacks, with 70 percent of their malicious activity targeting manufacturing. A lot of the success that groups like these have achieved in cyber extortion can be attributed to malicious business models like ransomware-as-a-service (RaaS) and sophisticated underground marketplaces where ransomware developers outsource operations to affiliates who execute the attacks. Affiliates do not require high-level technical expertise because the ransomware software has been developed and they can purchase access to systems and hackers for hire, which significantly lowers barriers to entry.
The DarkSide gang (now rebranded as REvil) offered customer service with real-time chat support andbrought in at least $60 million before it announced it was closing its operations. Investing in their business, ransomware groups are also funding research and development, which is fueling their industry as their extortion methods become more extreme. These are criminals, but they’re also savvy businesspeople, so manufacturers should expect them to continue to knock over vulnerable factory systems if they stand to make a handsome profit through ransoms readily paid by manufacturers who can’t afford to have their production ground to a halt.
What to Expect in 2022
Unfortunately, many manufacturers are still ill prepared to buffet these ransomware attacks before the adversaries have already stopped production. Dragos YiR analysis based on professional services engagements last year shows that 90% of manufacturers have limited visibility into their OT systems and the same percentage have set up poor network perimeters. Meantime, 80% of manufacturers have external connectivity exposed in OT systems and 60% utilize shared credentials that can easily be leveraged by ransomware groups to compromise systems.
Ransomware trends are likely to continue shifting as groups reform, reprioritize, and as law enforcement pursues them and takes them offline. As this evolution continues to evolve, Dragos analysts believe with a high degree of certainty that ransomware will continue to disrupt all industrial operations and OT environments through 2022, in manufacturing and beyond. Manufacturers should prepare now because ransomware actors’ extortion techniques will continue to grow in severity and intensity as adversaries deploy any means available to maximize their ransom profits.
To read more on OT cybersecurity trends, see the full Year in Review (YiR) report: https://www.dragos.com/year-in-review/
————————————————————————————————————
 Peter Vescuso is Vice President of Marketing at industrial cybersecurity provider Dragos and a member of the Manufacturing Leadership Council.
Peter Vescuso is Vice President of Marketing at industrial cybersecurity provider Dragos and a member of the Manufacturing Leadership Council.